What is Open Source Intelligence (OSINT)?
Ever wondered how much of your digital footprint is public? Spoiler: It’s way more than you think. Enter Open Source Intelligence (OSINT)—the art of turning scattered public info into actionable intel. Think of it as Sherlock Holmes meets Google, but with cooler tools and fewer deerstalker hats. Let’s break down what OSINT is, why it matters, and how it’s reshaping everything from cybersecurity to catfishing investigations.
OSINT isn’t just about stalking LinkedIn profiles or Googling your ex (though it can do that). It’s a structured process to collect, analyze, and weaponize publicly available data—social media, government records, blogs, even cat memes—into insights that help governments, companies, and even you make smarter decisions. Ready to geek out? Let’s dive in.
🕵️♂️ What Exactly Is OSINT?
Open Source Intelligence (OSINT) is the James Bond of data analysis: it systematically gathers intel from publicly available sources—like social media, news articles, or patent filings—and turns it into actionable intelligence. But here’s the kicker: raw data ≠ intelligence. OSINT only becomes valuable when it’s filtered through the intelligence cycle:
- Direction: Define what intel you need (e.g., “Is my company’s data leaking on the dark web?”).
- Collection: Scrape social media, forums, and public records.
- Collation: Organize the chaos into a usable format.
- Evaluation: Weed out fake news and biased sources.
- Analysis: Connect dots to uncover patterns (like linking orange prices in Paris to WWII bombings—true story).
- Dissemination: Share findings with decision-makers.
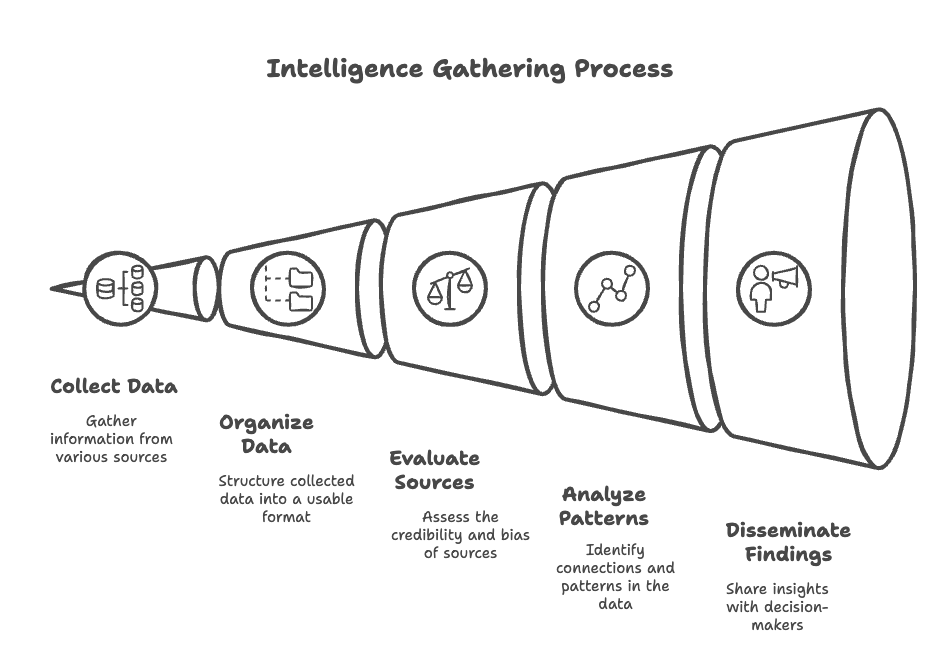
Without this cycle, you’re just another person with 50 browser tabs open.
Key Insight: The SANS Institute emphasizes that OSINT is not just data aggregation but requires critical thinking to transform raw data into actionable insights. For example, tracking a suspect’s digital footprint involves correlating social media posts, geolocation data, and blockchain transactions to build a comprehensive profile.
🌐 Where Does OSINT Come From?
OSINT sources are everywhere—literally. Here’s where pros look:
- Media: Newspapers, TV, podcasts, and blogs. Bonus: platforms like YouTube or Twitter / X (here’s how to search people on Twitter / X in 2025).
- Government data: Budget reports, court hearings, and speeches.
- Academic journals: Peer-reviewed papers and theses (nerd alert).
- Commercial databases: Financial records or satellite imagery.
- Grey literature: Patents, newsletters, and even that obscure PDF you found at 2 a.m.
Pro tip: Want to find someone’s employment history for free? Public records and LinkedIn sleuthing work wonders.
Deep Dive: The deep web (non-indexed content) and dark web (Tor networks) are goldmines for OSINT. Tools like Intelligence X archive controversial or deleted data, such as leaked VPN credentials or politically sensitive documents. Law enforcement agencies used similar methods to analyze 100GB of social media data during the 2021 U.S. Capitol riot, identifying suspects through geotags and usernames.
🛠️ Tools of the Trade
OSINT tools range from “I could’ve built this” to “Whoa, Big Brother is watching”. Here’s the toolkit:
- Maltego: Maps relationships between people, companies, and domains. Perfect for spotting shady connections.
- Shodan: Google for internet-connected devices. Yes, your smart fridge is probably on here.
- TheHarvester: Scrapes emails and subdomains. Ideal for finding LinkedIn profiles by email.
- Recon-ng: Automates web reconnaissance. Set it and forget it.
- FOCA: Extracts metadata from documents. Because PDFs spill secrets.
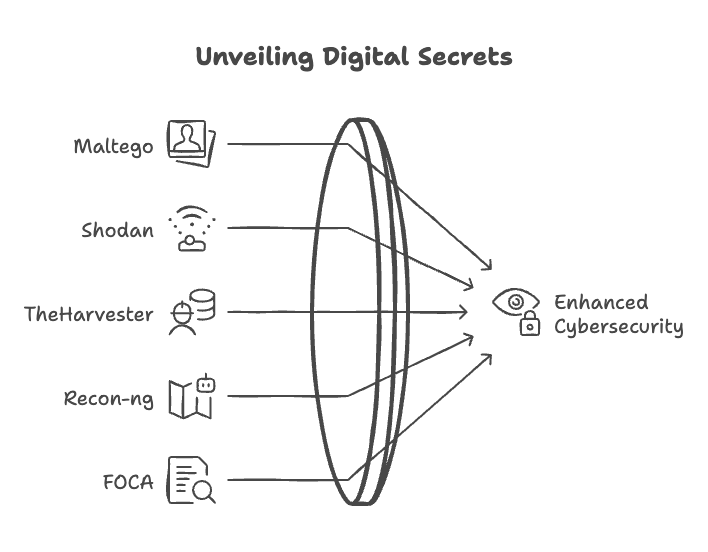
For a full list, check out the OSINT Framework—it’s like the Yellow Pages for spies.
Hidden Gems:
- Spiderfoot: Free tool for aggregating IP addresses, email leaks, and Bitcoin wallets.
- Social Links: An AI-powered platform used by law enforcement in 80+ countries to analyze 500+ sources, including dark web forums and blockchain ledgers.
- Google Dorking: Advanced search operators like
filetype:logorintitle:"admin"to uncover exposed databases.
💼 Who Uses OSINT and Why?
OSINT isn’t just for spies. Here’s who’s leveraging it:
- Governments: Tracking global threats or verifying intel from classified sources.
- Law enforcement: Solving crimes using social media trails (how to find phone numbers by email, anyone?).
- Cybersecurity teams: Spotting vulnerabilities before hackers do.
- Journalists: Fact-checking politicians’ “alternative facts”.
- HR departments: Vetting candidates’ employment histories or social media red flags.
Even social engineers use OSINT to craft convincing phishing emails. Stay vigilant!
Case Study: The FBI used OSINT to dismantle a human trafficking ring by correlating cryptocurrency transactions on the blockchain with social media recruitment posts. Meanwhile, cybersecurity firms like Imperva use Shodan to detect unpatched servers exposed to ransomware attacks.
📜 A Brief History Lesson
OSINT isn’t new—it’s just gone digital. Here’s the TL;DR timeline:
- 1941: The U.S. creates the Foreign Broadcast Monitoring Service to eavesdrop on WWII radio broadcasts.
- 1980s: The term “OSINT” is coined by the military to describe intelligence gathered from newspapers and public databases.
- 2005: Post-9/11, the CIA launches the Open Source Center to streamline public intel.
- 2025: The Department of Homeland Security adds a dedicated OSINT division.
The Evolution of OSINT
Key Milestones
1941
Foreign Broadcast Monitoring
1980s
"OSINT" Term Coined
2005
CIA Open Source Center
2025
DHS OSINT Division
Fun fact: Analysts once linked rising orange prices in Paris to bombed railway bridges during WWII. Mundane data, major insights.
Modern Evolution: With the rise of AI, tools like Social Links now automate data collection and analysis, sifting through 1700+ extraction methods to link aliases, phone numbers, and crypto wallets.
⚠️ The Dark Side and Speed Bumps
OSINT isn’t all sunshine and data rainbows. Challenges include:
- Information overload: Sorting signal from noise in a data tsunami.
- Ethical dilemmas: Just because info’s public doesn’t mean aggregating it is cool.
- Legal gray areas: Privacy laws vary globally (looking at you, GDPR).
Pro tip: Always ask, “Would I want this done to me?” before doxxing someone.
Real-World Pitfalls:
- Verification: A 2023 Frost & Sullivan report highlights that 40% of OSINT data requires cross-validation due to deepfakes or manipulated metadata.
- Timeliness: Criminals often delete evidence quickly. Automated tools like Collector screenshot social media posts before they vanish.
- Jurisdiction: A European court fined a firm €2M for scraping public LinkedIn profiles without consent.
🔮 The Future is Open
OSINT is evolving faster than TikTok trends. With AI-driven tools and real-time data streams, it’ll soon predict threats before they happen. But remember: With great data comes great responsibility.
Trends to Watch:
- AI-Powered Analysis: Machine learning models like Fivecast now flag extremist content on social media by analyzing linguistic patterns.
- Blockchain Forensics: Tools like Chainalysis trace crypto laundering routes, linking anonymous wallets to real-world identities.
- Real-Time Threat Prediction: The Pentagon’s Maven Project uses OSINT to predict geopolitical crises by monitoring news sentiment and satellite imagery.
Whether you’re a cybersecurity pro, a journalist, or just a curious soul, OSINT skills are your superpower. Start small—like finding a Twitter account by email—and level up from there.
🔍 OSINT FAQ
1. How can OSINT be used in cybersecurity?
Defensively, it spots vulnerabilities (like exposed databases). Offensively, hackers use it for social engineering. Always monitor your digital footprint!
2. What are the main challenges in OSINT?
Data overload, verifying source credibility, and balancing ethics with efficiency.
3. How does OSINT differ from traditional intelligence gathering?
OSINT uses public sources (social media, blogs), while traditional intel often relies on classified or human sources.
4. What tools are commonly used for OSINT?
Maltego, Shodan, and Recon-ng. For lighter tasks, try reverse email lookup tools.
5. How can OSINT be applied in law enforcement?
Tracking suspects via social media, verifying alibis with geolocation data, or uncovering financial crimes through public records.
Got more questions? Slide into the comments—we’ve got answers (and maybe a few cat memes). 🐱💻
Final Word: OSINT is the ultimate double-edged sword. It empowers truth-seekers but also equips malicious actors. As the digital landscape grows, mastering OSINT isn’t just a skill—it’s a survival tactic. Dive deeper with courses like SANS SEC497 or explore tools from the OSINT Framework to stay ahead of the curve.
Data nerd @ GetUser.ai. Been helping sales teams work smarter with data since 2018. I dig into the nuts and bolts of email verification, lead research—the stuff that actually moves the needle.